ProFuzzBench: Experimental benchmark for stateful network fuzzers
One of the key factors for progress in fuzzing research is the availability of benchmarks, that is, representative and well-defined experimental targets for applying heuristic techniques, and for obtaining reproducible and quantitative evaluations.
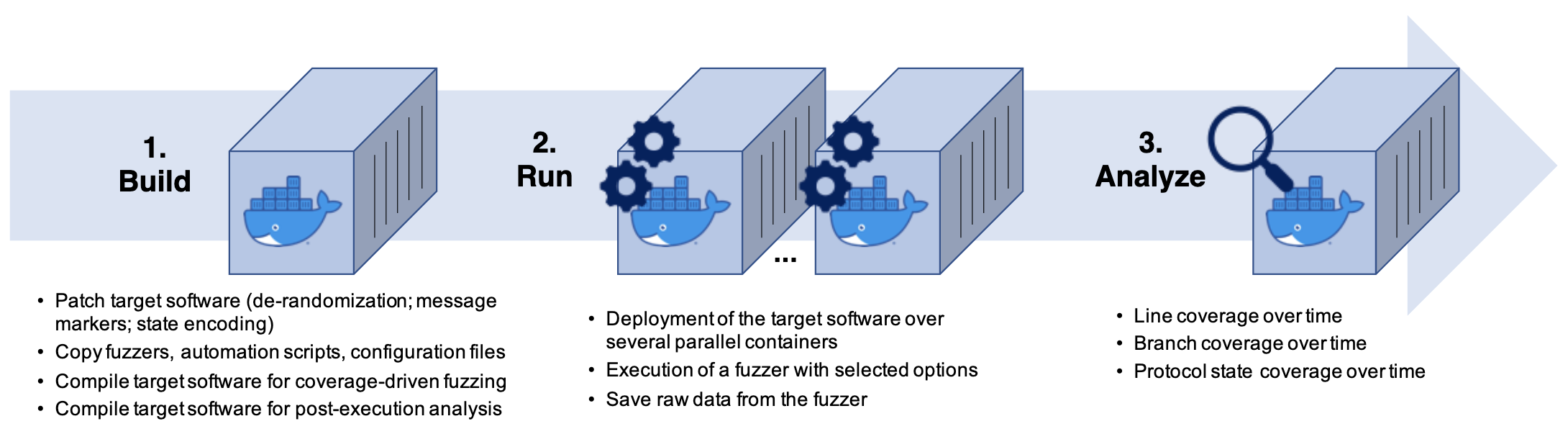
ProFuzzBench is a benchmark for stateful fuzzing of network protocols. This benchmark provides a suite of popular open-source programs that implement popular network protocols (selected on the basis of previous fuzzing research and commercial/open-source tools), with full automation of fuzzing experiments.
Getting the tool
The benchmark is available at: https://github.com/profuzzbench/profuzzbench
For more information
StateAFL: Coverage-Driven (Greybox) Fuzzer for Stateful Network Protocols
StateAFL is a fuzzer designed for network servers. It extends the original idea of the AFL fuzzer, which automatically evolves fuzz inputs to maximize code coverage. In addition to code coverage, StateAFL seeks to maximize protocol state coverage.
The aim of this tool is to contribute towards a completely-automated solution for stateful protocol fuzzing (similarly to what AFL was able to achieve for stateless programs) and to promote a wider application of fuzzing in real-world systems. The fuzzer does not require developers to implement custom message parsers for the protocol under test.
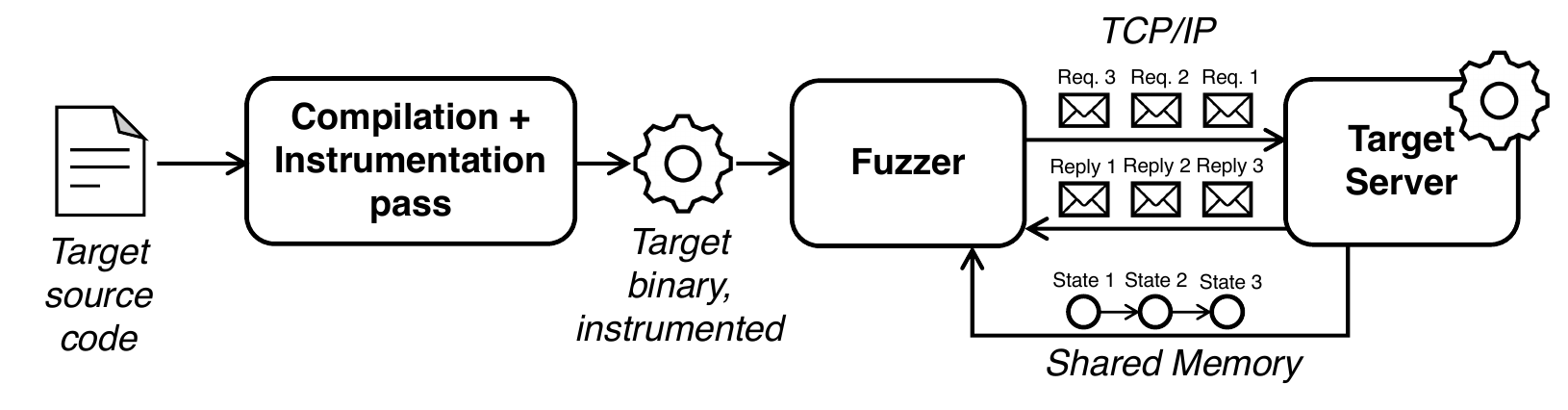
StateAFL automatically infers the current protocol state of the server. At compile-time, it instruments the target server with probes on memory allocations and network I/O operations. At run-time, it takes snapshots of long-lived data within process memory for each protocol iteration (see figure), and it applies fuzzy hashing to map the in-memory state to a unique protocol state.
Getting the tool
The tool is available at: https://github.com/stateafl/stateafl
For more information
EVIL: Exploiting Software via Natural Language
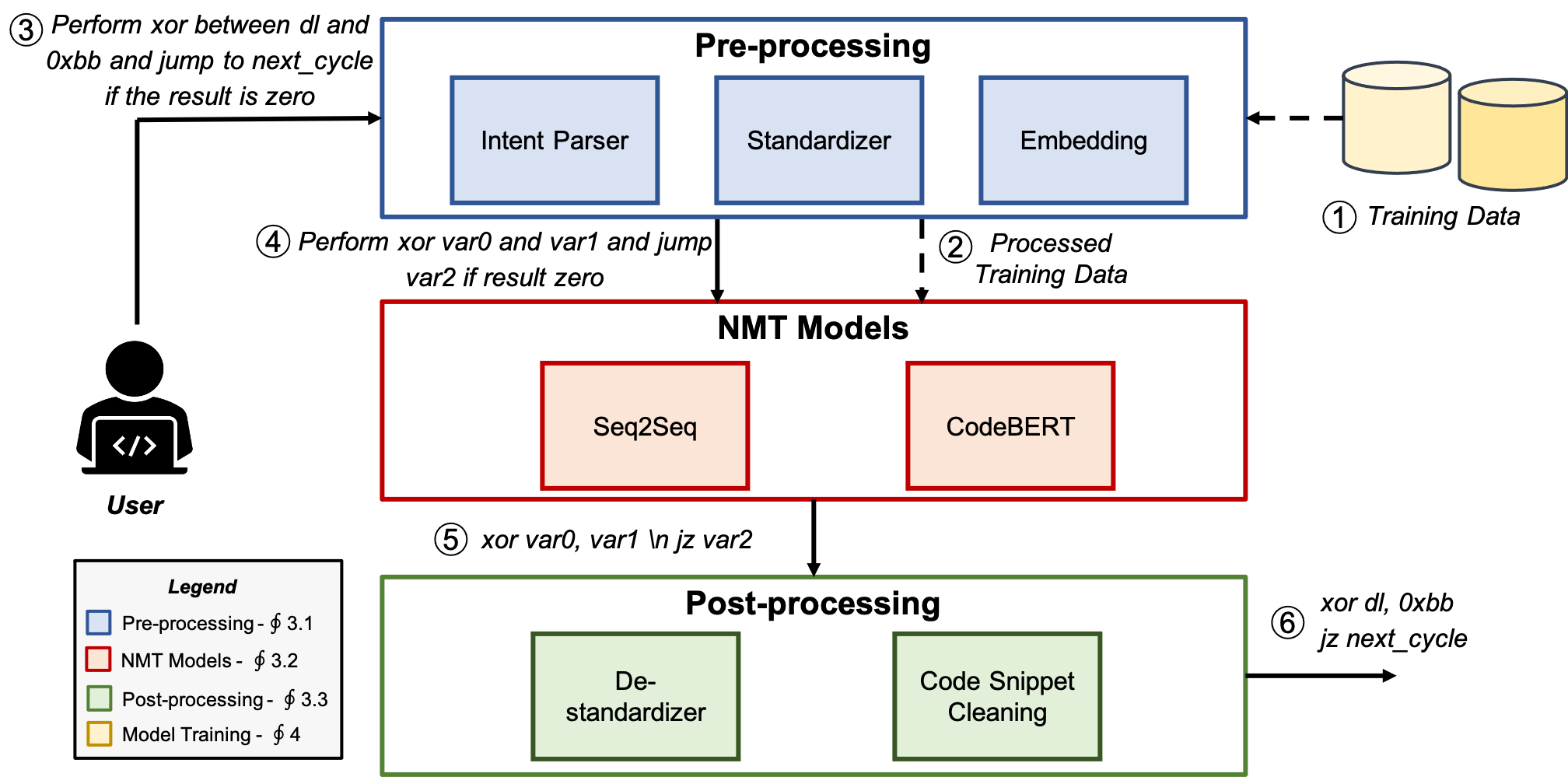
EVIL is an approach to automatically generate software exploits in assembly/Python language from their descriptions in natural language. The approach leverages Neural Machine Translation (NMT) techniques, and comes with a dataset of labeled shellcodes and exploits (Shellcode_IA32).
Getting the tool
EVIL is available at: https://github.com/dessertlab/EVIL
The repository also contains an updated version of the Shellcode_IA32 dataset, extended with offensive Python code.
For more information
- EVIL: Exploiting Software via Natural Language, ISSRE 2021
- Can We Generate Shellcodes via Natural Language? An Empirical Study, Automated Software Engineering journal
Chizpurfle: A gray-box Android fuzzer for vendor service customizations
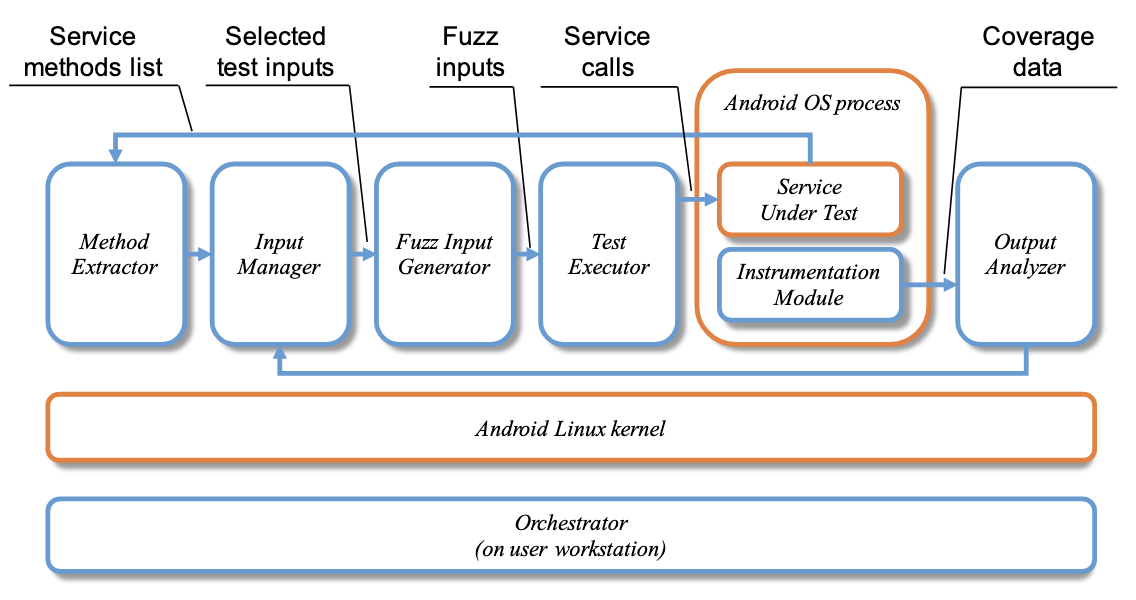
Chizpurfle is a gray-box fuzzer for testing vendor-specific (proprietary, closed-source) customizations of Android OS. It is designed to run on actual Android devices.
Getting the tool
Chizpurfle is available at: https://github.com/dessertlab/fantastic_beasts
For more information
- Chizpurfle: A Gray-Box Android Fuzzer for Vendor Service Customizations, ISSRE 2017
- Evolutionary Fuzzing of Android OS Vendor System Services, Empirical Software Engineering journal
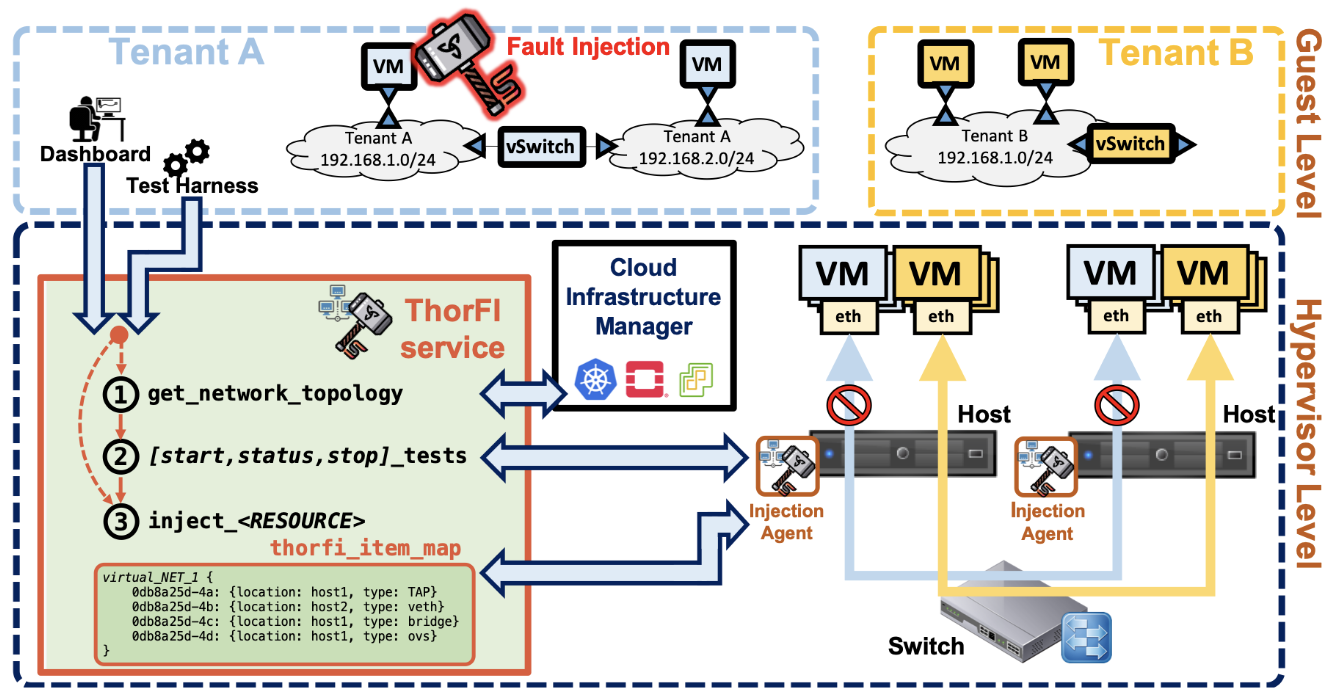
ThorFI: Fault Injection for multi-tenant cloud infrastructures
ThorFI is a novel fault injection solution for virtual networks in cloud computing infrastructures.
ThorFI is designed to provide non-intrusive fault injection capabilities for a cloud tenant, and to isolate injections from interfering with other tenants on the infrastructure. Currently, ThorFI supports the OpenStack cloud management platform.
Getting the tool
ThorFI is available at: https://github.com/dessertlab/thorfi
For more information
SAFE: SoftwAre Fault Emulator tool
Motivation
With the growth of software complexity, software faults (i.e., bugs) become a major cause of failures in computer systems. In spite of good software engineering practices, in most cases it is unfeasible to develop bug-free software.
Therefore, business- and mission-critical systems need to cope with residual software faults within software products. The injection of software faults consists in the deliberate insertion of bugs in a software component, for the following purposes:
- Validation of Fault-Tolerance Mechanisms: developers can evaluate how well fault-tolerance mechanisms (e.g., input checks, exception handling)
- Risk Assessment: anticipating worst-case impact of software faults (failure modes)
- Dependability Benchmarking: comparison of different systems or design choices (e.g., which off-the-shelf OS or library should be integrated in a system, from a dependability perspective)
How the tool works
The SAFE tool enables the injection of representative software faults in C/C++ programs for dependability assessment purposes. The tool injects the most common types of software faults based on the Orthogonal Defect Classification scheme (ODC), including assignment, checking, algorithm and interface faults.
First, the tool statically analyzes the target program, and builds an internal representation (i.e., an Abstract Syntax Tree) of the source code. Then, it automatically locates fault locations in the source code that are best suited to emulate real software faults. Finally, the tool creates a set of ".patch" files, each containing a faulty version of the code.
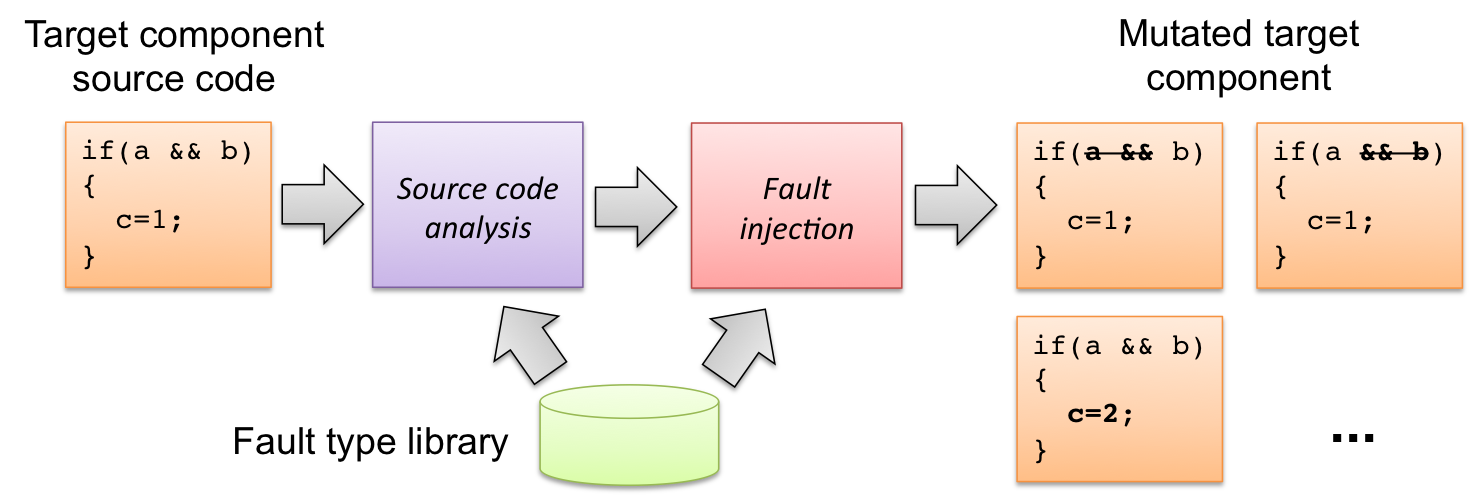
The fault injection process with SAFE
Getting the tool
The tool is freely available for educational and research purposes. To obtain the current version of the tool, please send me an e-mail (see contact info on the home page), indicating your affiliation, your research interests, and the reason for your interest on the SAFE tool. For commercial use and support, please contact Critiware s.r.l..
For more information
- Fault Injection for Software Certification, IEEE S&P, Jul/Aug 2013
- On Fault Representativeness of Software Fault Injection, IEEE TSE 39(1), 2013